March 2020, a month that will continue to resonate with most, every individual on the planet. The month that most countries across the globe implemented COVID 19 hard lockdowns within their countries. The month that changed the way we do business, in the most, rapid, and significant way, ever seen to this point.
Some will say that there was simply no interruption at all, as they were already well into a “business as usual” cloud adoption strategy within their business. Others struggled to come to terms with all or a large portion of their workforce, now working from a “home office”. Such “offices”, being the spare room, a study, the kitchen counter.
Two and a half years later, and I do believe we can all agree, this year and all the changes it brought, had a serious impact in escalation, of what can now be said, to be the number 1 risk, for most businesses anywhere in the world.

PREDICTABLY UNPREDICTABLE, THE CYBER RISK EVOLUTION
“Tomorrow is going to be predictably unpredictable”, (to quote Mr. Todd Nightingale Cisco Executive VP, in a recent Sunday Times article), really sums up the state of all things 2022, as we contemplate the future business landscape, two and a half years from ground zero, where COVID 19 lockdowns, hit the world and changed it immeasurably.
The changes that the pandemic brough, in every aspect of life and livingness, are still evolving and the impacts still being evaluated. However, the major impacts relating to, how we work, I do believe is a change that will stay with us permanently. Perhaps not in every business, but certainly in many.
The Work from Home event was the most rapid change ever to occur in business operation, on a worldwide scale in known history. This change impacted many things, at both personal and business levels, but very specifically impacted IT departments and management of information, and most particularly, the way we need to think about our Governance, Risk and Compliance strategies, including Continuity of Business and Business Resilience strategies.
Given the speed of most of the Work from Home implementation strategies, adopted by businesses, many failed to effectively carry out, a complete, context informed, business impact assessment, and consequence analysis in the fine detail that was really needed. As a result, many organizations who had, to that point, largely on-premises IT infrastructure or an evolving cloud hybrid, rapidly migrated, into hybrid cloud or total cloud adoption, in a very short time. They then, through the pandemic, over the last 2 years, maintained a “management by crisis” business as “unusual” strategy, reactively dealing with event after event, as the cybercrime wave evolved.
During this last 2 years we have see an explosion of cyber risk, resulting in company data compromise, loss, extortion, ransomware attacks, information leakage, like the world never really thought was possible in 2019, certainly not on the scale we see today, but, sadly, is now a daily norm in 2022.
However, what has, unfortunately, not occurred, is a robust evolution in IT GRC and enterprise GRC approach, over the last 2 years, to match the cyber risks growth path. A lot of technology adoption might have occurred, with a fuzzy comfort level of, “I’m pretty sure we are secure”, yet organizations still get severely compromised. Why?
Many organizations lack the GRC, (governance, risk, and compliance) maturity levels needed to deal with the scope of risk as the world was in 2019. For the most part, they certainly are not ready for the unknown scope of the unpredictable, rapidly evolving and changing risks of 2022 and beyond.
So, what then is the answer?

THE CHALLENGE
Ransomware attacks continue to evolve at a pace that outranks most business’s ability to keep up and keep their information secure. This has increased exponentially with most businesses, at a scale that few really want to confront or admit. There is no business that can honestly say that cybercrime is not a number one risk concern right now. Work from Home strategies, which are now evolving into hybrid work schedules, along with new emerging risks, of high fuel costs, supply chain disruptions and shortages, emergence of digital currencies and digital exchanges, branchless banking and more. All of which should have significantly evolved the “Context of the Organisations” evaluation assessments, as should be, being contemplated, in effective Risk Management strategies. However, this is not occurring, or not occurring effectively enough, given the magnitude of contextual change in the risk universe. Many Risk and GRC professionals have grappled with bringing an understanding, to the business as a whole, of the critical value of a Context of the Organisation Impact assessment. An activity that should be occurring as a business-as-usual tool, every time a key change occurs in the business. Yet maturity benchmark results, statistically indicate that most business executive and management teams, don’t know what this tool is, never mind being consistently effective in continuous use, in the business, as part of strategy and business planning at operational levels.
The Security Focus Africa survey for “State of Ransomware 2022”, indicates that 51% of the South African companies included in the survey, were hit by a ransomware. Many of which succumbed to paying the ransom, yet still remained compromised in getting their data back.
Our ongoing consultations with clients, within the processes of closing identified security and cyber risks gaps, indicate that even though there may be good back up procedures and quick restoration of data, which would avoid paying the ransom, such clients have then been subject to extortion, whereby data has been encrypted and taken by the ransom attackers, who then contact the affected company and threaten to publish sensitive information on open internet and social media forums. Thus, the ransom attack becomes extortion.
We often are told by management teams, MD’s, CEO’ s and business owners, that their IT teams have told them, that security is under control and well managed. When pushed for specifics, this conversation takes a very different course, where senior management become less confident that they “really” know, transparently, with an unbiased slant, the state of security and cyber risks resilience levels, within their business.
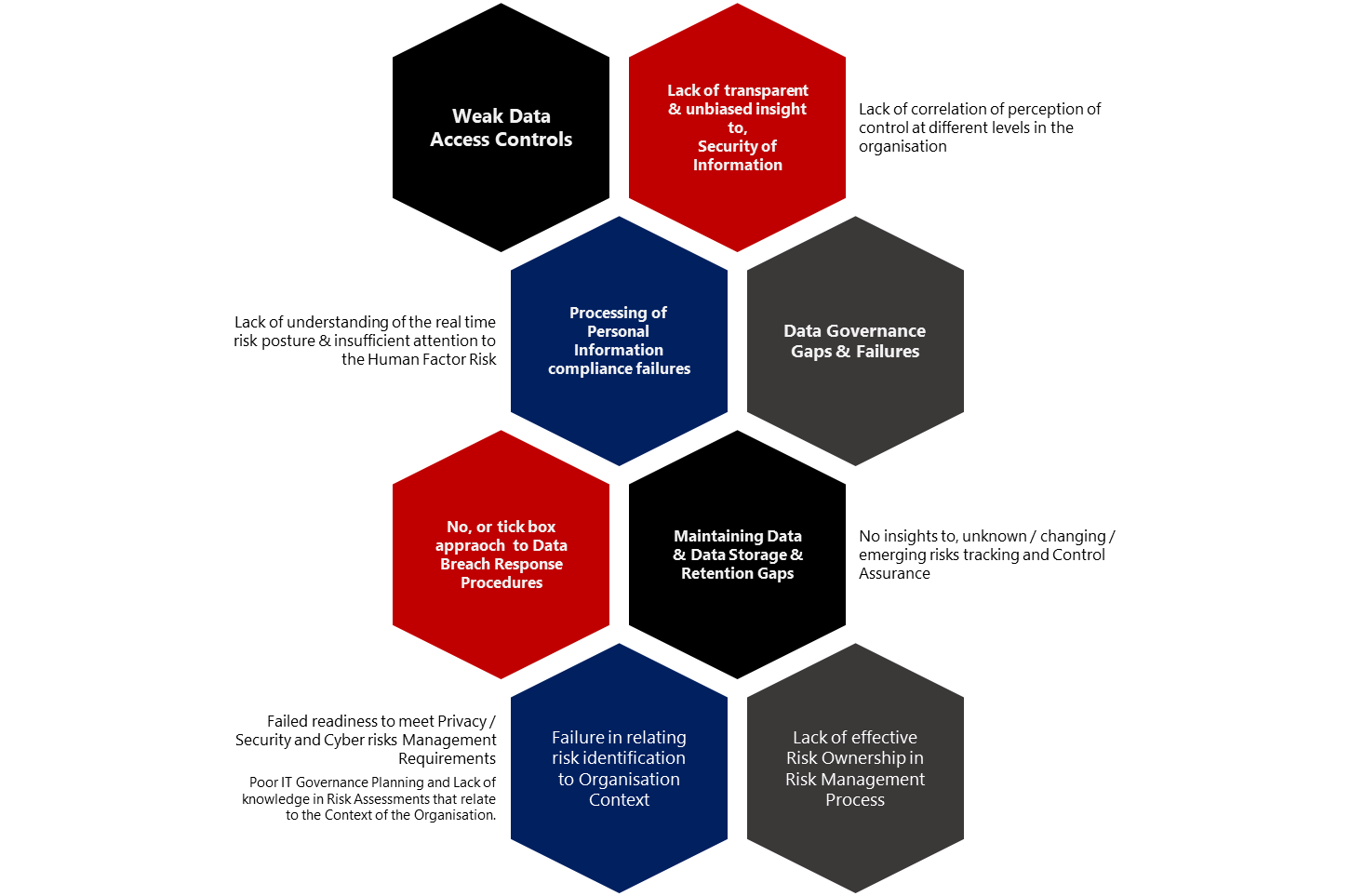
In conducting GRC and related, cyber risk and information security and data privacy maturity evaluations, we consistently see the following risk areas, with low maturity scores.
Common Cybersecurity | Data Privacy | Information Security | IT Governance Maturity Gaps
Maturity Evaluation GRC Verticals Covered by Assessed Respondents:
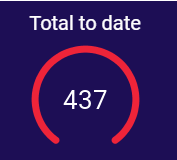
Of the 437 maturity evaluations conducted by the RUBIQ Team to date, the most significant area of identified weakness, is in the area of, a structured approach to Information Security Management. Many organisations would significantly benefit from the implementation of an ISO 27001 aligned ISMS Information Management System. However, few have taken the time to effectively design and implement an ISMS. There is no doubt that we see exceptional improvement in the management of IT Governance, Data Privacy Management, and an overall maturity across the organization, with companies that have focused on implementation of an ISMS, which includes the scope of Data Privacy and Cyber Security.
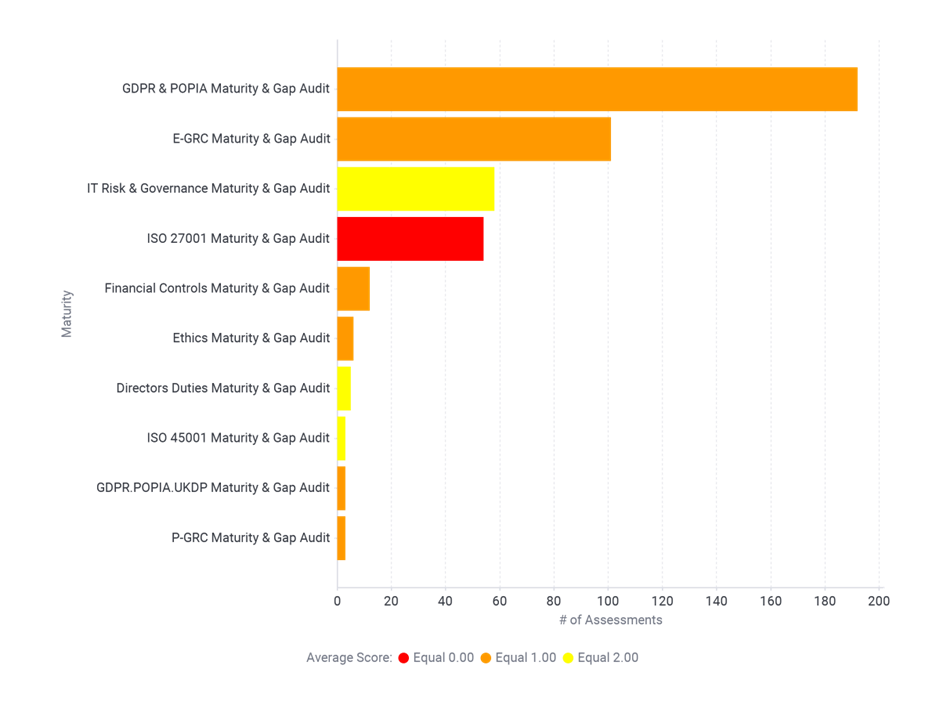
Given the hype around POPIA in 2021, many organisations opted to conduct Data Privacy and POPIA / GDPR maturity assessments, which does make up the bulk of the data set. Within the maturity evaluations completed by companies on Data Privacy, we included a key focus on Security of Information. We then cross referenced this data with the alignment in the company to ISO 27001 clause assessment and the ISO 27002 Annexure A Controls review, and the results were universally very poor. Giving clear indication of the very low maturity that exists within organisations in this regard.
Coupled with the evaluations we conducted during the maturity assessment, related to the organisations approach and general practice to Good IT Housekeeping practice, which included an assessment related to Ransomware and Data Breach susceptibility, the results were again very poor, with most orgranisation showing high probability of a ransomware attack, given their cyber risks scores and demonstrated maturity levels for protection of information and management of Data Privacy and Cyber risks.
The Maturity evaluation benchmark data further highlights the averagely low maturity levels related to several of the other enterprise GRC verticals, such as Ethics, People Risks, Financial Controls and EGRC approach overall, to Governance, Risk and Compliance management, as well as maturity related to Internal Audit.
The spread of companies included in the Maturity Evaluations to date, covered a board spectrum sampling, of various sectors and industries, as well as an inclusion in the sampling of small, medium, medium large and enterprise organisations.
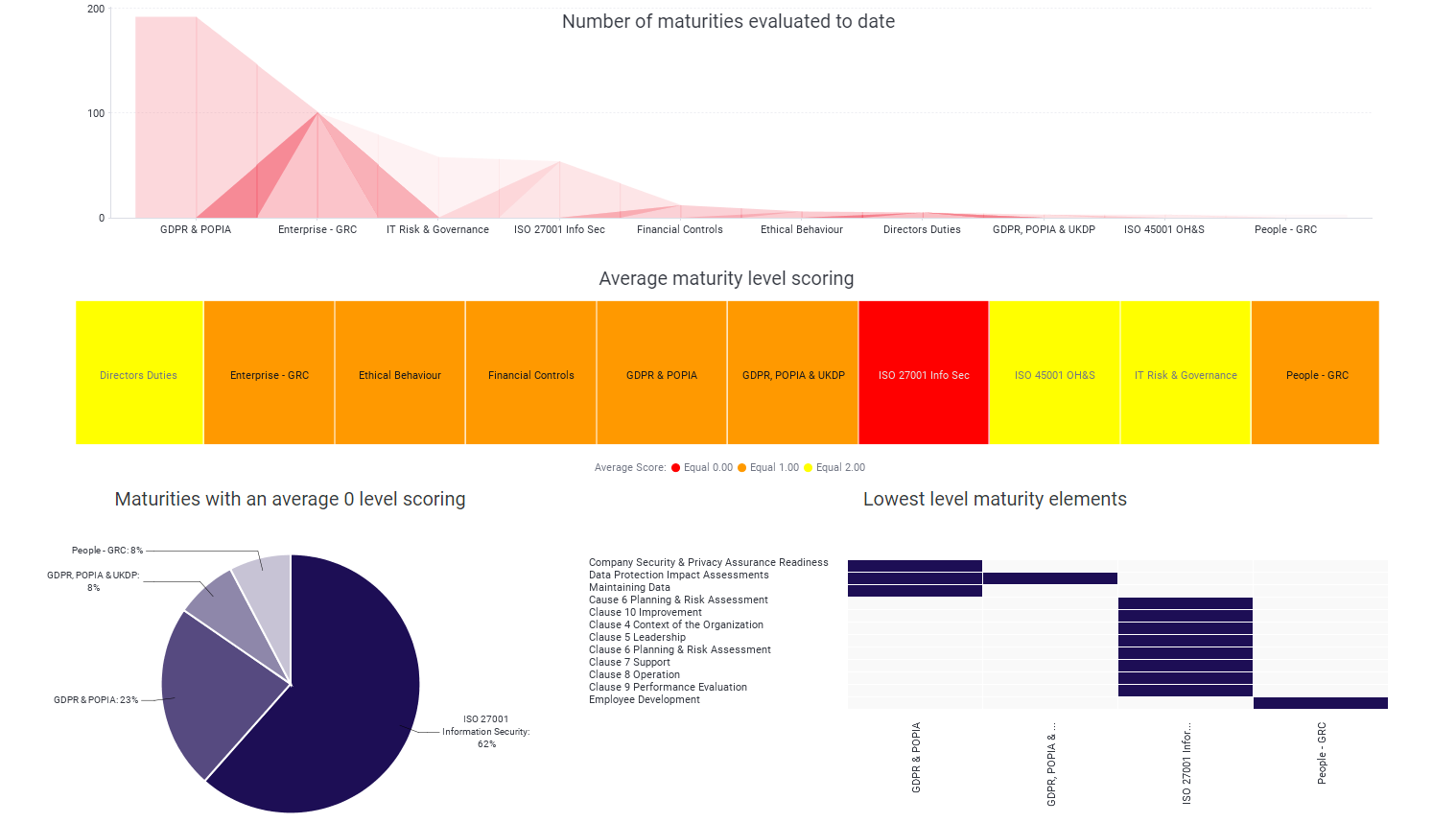
Key findings, we should take note of, relate to the following aspects.
A SOLUTION
RUBIQ is a cloud-based platform that uses cutting-edge technology to provide a genuinely unique, comprehensive, and dynamic governance, risk, and compliance (“GRC”) management solution for any sized company, wherever in the world. RUBIQ is easy to use, has a lot of, ready to use knowledge repositories and information and features, and is, relatively, inexpensive, regardless of the size of your company, without negating, the sophistication of the insights, that our approach brings to your business.
RUBIQ is the culmination of the combined experience of GRC knowledge and expertise and GRC Technology know-how on the part of the Founder, CEO and key subject matter experts, that exceeds 75 years.
The RUBIQ Team has developed a unique and proprietary approach, to addressing the challenges in IT GRC. This approach has been developed in line with the key discoveries made from our GRC and IT GRC Maturity assessment initiative, that has been running for the last year and half. The Maturity assessment initiative has led to the fine tuning of our Advisory / Solution programmes, which makes unique use of both a select set of technical insights, analysis, and data governance audit tools, as well as the body of Subject Matter Expert, developed content, where we have worked with leading advisory specialists in their fields. The RUBIQ Advisory Programmes are broken down into 3 initial phases, with a final 4th embedment and enforcement phase.
The results of all 4 phases, fully completed and embedded are:
WHY CONDUCT MATURITY EVALUATIONS?
What are Maturity Assessments?
In a nutshell…
It is well documented that Companies with a high degree of GRC / IT GRC, integrated maturity, achieved within their organisations are:
Unfortunately, very few organisations take the time to effectively develop a GRC / IT GRC roadmap and supporting strategy, against a proven and workable, GRC Maturity Model.
Take the free online quick assessment, as a quick test of your current IT GRC status.




